Thursday, March 30, 2023
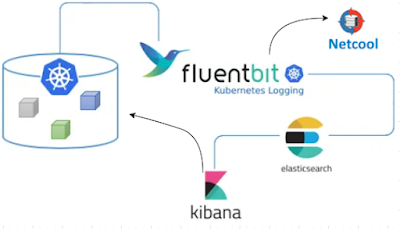
Sending Kibana (free/open source) Alerts via Webhook Using Fluent-Bit (free)
Wednesday, March 29, 2023
Tunneling X11 over SSH as a different user
Background
Solution
Ensure X11 tunneling is configured for your session:
Open the session (connect to the remove system) and ensure that your xauth exists and your local display is set so you can get your MIT-MAGIC-COOKIE:
[franktate@linux1 ~]$ echo $DISPLAY
localhost:10.0
[franktate@linux1 ~]$ xauth list | grep :10
linux1.gulfsoft.com/unix:10 MIT-MAGIC-COOKIE-1 a229706ccb496af61501ea25a95488
[franktate@linux1 ~]$
Note how your display number is used to identify the appropriate MIT-MAGIC-COOKIE
Ensure that an X application can connect to your Windows X server by running xterm or some other application.
Switch users and set the MIT-MAGIC-COOKIE:
[franktate@linux1 ~]$ su - db2inst1
Password:
-bash: TMOUT: readonly variable
[db2inst1@linux1 ~]$ xauth add linux1.gulfsoft.com/unix:10 MIT-MAGIC-COOKIE-1 a229706ccb496af61501ea25a95488
[db2inst1@linux1 ~]$
Run xterm or some other X application to be sure X is tunneled correctly. Assuming that works, now connect from the first machine to another.
SSH to the next hop host and get your MIT-MAGIC-COOKIE
[db2inst1@linux1 ~]$ ssh -Y frank2@linux2
frank2@linux2's password:
Last failed login: Sat Feb 23 16:17:29 EST 2019 on pts/0
[frank2@linux2 ~]$ echo $DISPLAY
localhost:10.0
[frank2@linux2 ~]$ xauth list | grep :10
linux2.gulfsoft.com/unix:10 MIT-MAGIC-COOKIE-1 2d31b43034bfc9da1c0d2848c1b718
[frank2@linux2 ~]$
Run xterm or some other X application to be sure X is tunneled correctly.
Switch users and set the MIT-MAGIC-COOKIE
[frank2@linux2 ~]$ su - db2inst1
Password:
[db2inst1@linux2 ~]$ xauth add linux2.gulfsoft.com/unix:10 MIT-MAGIC-COOKIE-1 2d31b43034bfc9da1c0d2848c1b718
Run an X application like xterm to validate that it's working.
Modify kibana.yml after deploying Kibana with Helm
kubectl exec --stdin --tty kibana_podname -- /bin/bash
you'll find that there's no editor available (like vi or even ed). You can cat config/kibana.yml, but the comments state that it is auto-generated. So what are you supposed to do to add an a setting to the file? For example, you might need to add a value for xpack.encryptedSavedObjects.encryptionKey so you can configure alerting.
The solution I came up with is a multi-step process:
1. Get the default values.yaml file for the chart and store that in a file with the command:
helm show values elastic/kibana > /tmp/kibana.yaml
2. Edit that file to add a section for kibana.yml under kibanaConfig. Originally, kibanaConfig is empty (set to {}). You need to change it to be something like:
helm uninstall kibana
3. Then install the helm chart again with:
helm install kibana elastic/kibana -f /tmp/kibana.yaml
And that's it. Your changes will be applied and you're good to go.
I'm pretty sure there's a way to create a configMap and reference it, which would then allow you to just delete the pod to have it re-read the configMap, but I haven't figured out those exact details. Maybe in another post.
Tuesday, March 21, 2023
Installing .pak Files on WebSphere Application Server 8.5.x
Background
Solution
Thursday, March 16, 2023
Installing additional software on the Rancher docker container
If you read one of my previous posts to install Rancher on a single docker container, you may have found that it doesn't include several commands like ping, netstat, ss, and even apt. And if you run 'uname -a', you might think that the image you're in is Ubuntu, but it's not. It's SUSE Linux (the same people who maintain Rancher), and the package manager there is accessed via the command 'zypper'. So to install several of the tools you know and love, run the following
zypper install net-tools iproute2 bind fping lsof
That's it. Now you have a few more tools for debugging.
Wednesday, March 15, 2023
Installing Rancher in a Single Docker Container on Ubuntu 20.04
This is MUCH easier than my last couple of posts because this just takes one step after you configure your OS. Rancher is a cloud native (runs on its own K8s/K3s cluster) K8s manager and container orchestration platform. It is a competitor to Red Hat OpenShift and VMWare Tanzu.
This solution is for a DEV/practice environment.